Fraud involving a card that is not physically present is known as CNP (Card Not Present) fraud.
The most typical forms and methods of CNP fraud include Internet and smartphone sales, phone payments, scanning, and evaluation.
Since the transaction is completed through an online mode, merchants are unable to personally authenticate that the individual is who s/he claims to be.
Hence, it’s crucial to obtain as much data as possible about your consumers to reduce risk.
Acquiring user data, examining user actions, and identifying dubious CNP transaction details can help in CNP fraud detection and prevention.
Using IP (Internet Protocol) address identification, device fingerprinting, or social media search, this information should be improved.
9 Guidelines to decrease CNP fraud
It’s critical to comprehend the ideal strategies for safeguarding your company against CNP fraud because culpability frequently rests with merchants, payment service providers, or the victim’s financial institution.
To assist you in identifying genuine customers and fraudsters, there are several contemporary solutions.
1. Gather all the client information you can
In general, it is better to get more consumer information. This is valid for card transactions, branding, and sales, as well as, the prevention of bank fraud.
Using the same data that enables you to verify user IDs or contest a dispute, you can drive sales, boost cross-selling, and optimize segmentation.
The basic information categories you ought to compile are:
- Inbox address
- The CVV (Card Verification Value) code from a bank card
- Payment address
- Information pertaining to the registration device
- IP address
- Call-in number
There are now three primary interfaces where you can collect that data: during user registration, signup, and at that point where bank card payments are accepted.
While it is required of you to adhere to the latest SCA (Strong Customer Authentication) practices, there is still a lot of information you can gather. User gadgets, contact numbers, and email accounts can be quite helpful in weeding out malicious entities at the very least, proving they’re problematic users.
Refusing questionable transactions that might be blatant instances of CNP fraud is made simpler with the more information you gather about a person.
The main problem here is gathering data without putting the customer through too much hassle, which might reduce conversions and revenues.
2. Request further authentication
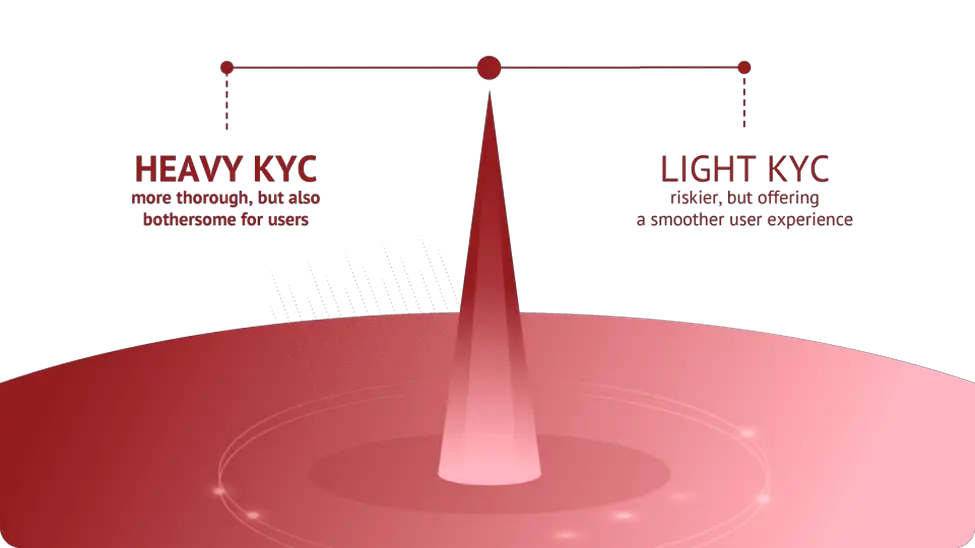
You must have all the information necessary at this point to categorize users, depending on their risk levels. It’s essential to minimize the risk by requesting additional authentication information.
When we read these tips for reducing card not present fraud, we learned that the above process is referred to as light and heavy KYC (Know Your Customer). You can implement rigorous authentication procedures when you have reached your threshold. This implies that legal customers will experience the least amount of friction when making purchases, but potential CNP criminals will find it more difficult to circumvent the requirements.
While using both mild and severe KYC to stop CNP fraud, you must strike the ideal mix between thorough and superficial KYC. In reality, you should start by allowing simple KYC capabilities, such as email analysis, IP analysis, and device fingerprinting.
You can then activate extra authentication procedures like ID (Identification) verification, 2FA (Two-factor Authentication), or credit card preauthorization – if you discover enough cause for concern.
By alerting fraudsters that you are suspicious, you keep your customers satisfied and deter CNP fraud. However, without the proper framework, automating flexible KYC at scale can be difficult.
3. Use data augmentation
After reading the first and second advice, are you wondering, “How can I gather additional information without causing friction?”
Augmentation of data is the solution. It makes sense that these solutions are now utilized by both banking firms and eCommerce companies. Simply said, it is a technique that employs one data checkpoint to gather information from outside sources.
For example, a user’s email address may be utilized to register for social accounts after analysis.
Similar to this, you can check a mobile number to see if it’s a smartphone or landline and its location is in which nation. All these information aids in identifying unusual disparities.
The best part is that, with the correct tools, this can be completed almost rapidly and without any further verification from the users.
Data enrichment could be concealed from the cardholder, lowering the risk without impeding the correct clients too much.
The main difficulty is synthesizing data from logical sources and recent, open-source databases. For example, by adhering to GDPR (General Data Protection Regulation) standards and connecting an email account to the customer’s active social media profiles.
4. Utilize the best practices for data protection
You must still safeguard the consumer’s credit card data even while they aren’t beside you.
In actuality, this means utilizing SSL (Secure Sockets Layer) and other internet security technologies, particularly on sites that gather sensitive data like credit card numbers, SSNs (Social Security Numbers), or addresses.
Information that is exchanged between employees or clients and your site should be encrypted as effectively as feasible.
Data, which is protected and encoded, is less prone to end up in the wrong hands, thereby lowering overall fraud.
Due to increasing expansion, keeping backups and setting protective hardware and software components can be expensive. It is the issue that professionals in the field cite most frequently.
5. Examine weird behavior
Ideally, you have sufficient knowledge at this point to begin learning about consumer behaviors.
There are a couple of universal red flags you should watch out for, even though what is deemed suspicious can vary from merchants to payment processors.
Fraudsters frequently work quickly and string together a number of compromised card numbers in order to collect as much money as possible. This indicates that specific characteristics in their behavior indicate digital fraud. As the merchant requires real-time behavior analysis, doing this without a suitable risk management plan in place is highly challenging.
6. Beware of incredibly little transactions
Not every fraudulent amount paid to your company will have an immediate effect on you.
Fraudsters may occasionally use you to verify a card, typically by making small purchases of goods or services.
Naturally, if the payment goes through, scammers may possibly utilize the same card to buy more expensive things, which can eventually harm your company. Quick identification of cards can aid in preventing fraudsters from exploiting stolen card information for larger purchases.
Monitoring minor deals that might otherwise slip from your notice is the biggest challenge in this strategy.
7. Review gift cards

Gift card theft is a frequent issue that coexists alongside CNP fraud.
Coupons are frequently activated using intercepted payment information by people who want to convert stolen goods into money as soon as possible. They then quickly sell these online delivered earnings in an open marketplace.
It pays to be extremely careful if your business has a loyalty scheme or provides gift cards as products or payment methods.
By raising the bar for scammers who seek to use gift cards fraudulently, CNP fraud may also be reduced.
The main problem here is providing enough payment options and loyalty schemes while preventing bonus misuse.
8. Contest chargebacks
The issue of amicable fraud is one facet of CNP fraud that we haven’t fully discussed before. There’s nothing nice about it, as you would already be aware. Transactions made with a CNP that could harm your business happen when:
- Customers withdraw from a transaction and assert that it was a fraud.
- Users utilize the actual card to attempt to trick the algorithm by requesting a chargeback.
- Members of the family use the card to make purchases without permission.
It is evident from these examples that the chargeback was the customer’s responsibility.
If you possess all the necessary documentation to support your claim, providers and financial institutions are quite adept at backing enterprises.
With richer data at your disposal, what are your options? Suppose, you use a social media analytical tool. You notice that some consumers had claimed they never obtained the item but they posted images of it on Facebook and Instagram. Talk about being caught by surprise.
Chargeback disputes, which are sometimes referred to as friendly fraud, could be won if you already have the necessary information on hand.
The main problem is gathering the appropriate information at the opportune point.
9. Design risk scoreboards
Assessing risk and establishing your thresholds are the key to preventing CNP fraud. In order to forecast who might be a problematic consumer, you sometimes need to have adequate information on fraudsters.
Risk scoreboards, that can let you group customers based on common data, behavior, and risk scores, are one practical approach to do so. We won’t get into too much technical information here because the sophistication of these scoreboards, which employ predictive methods, can vary substantially.
Scoreboards serve as a great method to spot fraud, however, you do it — using a manual process or an automatic one — and thereby lessen the potential harm.
Building risk models enables the extraction of information about dangerous users and the early detection of fraud.
The main difficulty is that risk scoreboards are intricate mathematical methods that can be difficult to construct manually.
Conclusion
Being ready, equipped, and aware is the best method to reduce the likelihood of CNP payments being fraudulent, just as it is with several other fraud schemes.
This stands true whether you employ a comprehensive end-to-end fraud protection solution or numerous levels of security using various techniques.




